Evolving Tides: Maritime Security and Cybersecurity in 2025 thru 2026
As someone who's spent decades knee-deep in industrial control systems and cybersecurity, starting way back with instrumentation and evolving into teaching International Society of Automation ("ISA") ISA/IEC 62443 OT security courses—I've seen how ports like Houston are the beating heart of global trade.
The port of Houston handles massive cargo volumes each year, with public terminals alone processing a record 53 million short tons in 2024 and showing strong 6% growth through late 2025, putting full-year figures on track to approach or exceed 56-57 million short tons. When factoring in the broader Houston Ship Channel ecosystem—including more than 200 private facilities—the total waterborne tonnage routinely surpasses 300 million short tons annually, making it the nation's largest by far. This immense scale isn't just a hub for energy (petroleum, refined products, LNG) and chemicals/petrochemicals, which dominate due to the region's industrial complex; it's a prime target in today's threat landscape, with known vulnerabilities to cyber intrusions and supply chain risks.
Through my work in InfraGard Houston, CG AMSC for the outer continental shelf, and on multiple advisory boards, I've had front-row seats to discussions on how we safeguard these vital assets. In 2025, maritime security isn't just about patrols or fences anymore; it's a tangled web of physical risks, cyber intrusions, and hybrid attacks from nation-states, cyber criminals, and those sneaky advanced persistent threat groups ("APTs"). Let me break this down, drawing from what I've learned instructing folks on modern OT vulnerabilities, and blend in the latest from credible sources to paint a clear picture.
The Bigger Picture of Maritime Security Today
Maritime security has always been about keeping the seas open and safe, but lately, it's gotten a lot more complicated. Take the United Nations Security Council debate back in August 2025—it zeroed in on prevention, innovation, and teaming up internationally to tackle emerging threats. I remember similar talks in my InfraGard and government circles, where we stress how global cooperation is key, especially for chokepoints like the Red Sea, South China Sea, and Panama Canal. A report from November 2025 highlighted ongoing tensions in the Panama Canal from drought and politics, plus beefed-up Chinese presence in the South China Sea, and even with ceasefires, the Red Sea's still dicey. For Houston, where so much of our cargo ties into energy exports, any hiccup there hits home hard. Interestingly enough, I've advised on secure systems for chemical sectors that rely on these routes—disruptions aren't just delays; they can cascade into supply chain nightmares.
The U.S. bumped up maritime security in its 2025 National Security Strategy, putting a spotlight on free navigation and protecting those key passages. It's a smart move, especially with hybrid threats on the rise—think physical sabotage mixed with digital hacks. Taiwan's 2025 National Ocean Policy expanded to cover non-traditional stuff like cyber security, which mirrors what I've pushed in my trainings: you can't secure the seas without securing the systems running them. On the exercise front, NATO's MARSEC-25 in October 2025 worked on getting allies in sync, while SEACAT 2025 in Southeast Asia used tools like SeaVision to boost monitoring. From my perspective, these drills are crucial; I've trained National Guard units in Cyber Shield exercises, and it's the same principle—practice makes resilient.
Tech's changing the game too. The Inmarsat Future of Maritime Safety Report for 2025 dug into distress signals and vessel weak spots, showing how AI and satellites are spotting threats faster. But here's the rub: those same tools can be turned against us if not locked down properly. In my article "The Paradox of Security," I talked about how the most secure system is one that doesn't exist—over-reliance on tech without safeguards is asking for trouble. (To review "The Paradox of Security" article in the Port Bureau News from last year, click here.)
Diving into Maritime Cybersecurity
Ports are going digital at breakneck speed globally—automated cranes, real-time tracking, you name it—and that's opened up a Pandora's box of cyberrisks. An August 2025 piece from Help Net Security flagged rising issues like ransomware, malware, spying, and even jamming GNSS systems. The U.S. Coast Guard stepped up with a January 2025 rule requiring cyber plans, drills, and dedicated officers at facilities. They followed it with an April alert on foreign meddling in port gear and networks. As an ISA Fellow, I've been hammering home these points in classes: without solid incident response, a breach can shut down operations, just like NotPetya did to Maersk years ago.
NATO's CCDCOE brief this year pushed for tailored intel sharing in the sector, noting ports handle 80% of world trade but are wide open to cyber hits. ABS Consulting’s early 2025 outlook pegged AI attacks and OT flaws as big worries. In Houston, where we deal with petrochemicals, these aren't abstract—I've consulted on systems where a cyber glitch could mean environmental disasters. But what keeps me up? It's how these digital threats bleed into physical ones. That said, it’s worth noting that Houston's pilots, navigating in and out through Galveston Bay, lean heavily on skilled visual piloting rather than over-relying on tech. They use sight lines, ranges, and on-scene judgment for safe transits, with tools like AIS mandated as operational aids—not primaries—especially when managing restricted visibility (which may trigger suspensions or daylight-only requirements) or for widebody vessels often limited to daylight hours. This human expertise adds a layer of resilience against tech disruptions.
Nation-State Actors: The Heavy Hitters
Nation-states are the pros in this arena, often mixing cyber ops with real-world muscle. A CSIS report from October 2025 drew parallels to incidents like the Colonial Pipeline ransomware attack, showing how cybercriminals—often operating from safe havens in adversarial nations like those in the CRINK group (China, Russia, Iran, North Korea)—target critical infrastructure for economic disruption. Russia, China, Iran—they're the usual suspects. Russian crews have hammered Ukrainian ports, while China's blending cyber snooping with South China Sea maneuvers.
The 2022 Nord Stream blast was a wake-up call on hybrid attacks against underwater infrastructure—attribution's tough, responses even tougher. AWS noted in 2025 that state actors are now peeking into ship CCTV and more. For us in Houston, foreign tech in our ports could leak cargo intel straight to adversaries. NATO's July 2025 warning on European port hacks exposed those gaps. And don't get me started on geopolitics—pro-Palestinian hacktivists using AIS data to harass Israeli ships? That's activism crossing into state-like ops, and it could spill over to our allies.
In my time in my work and volunteer roles, I've seen how these actors probe for weaknesses. It's not just about stealing data; it's disrupting flows to gain leverage.
Table One: Seven Aspects, APTs, Cybercriminals (2025-Ayala)
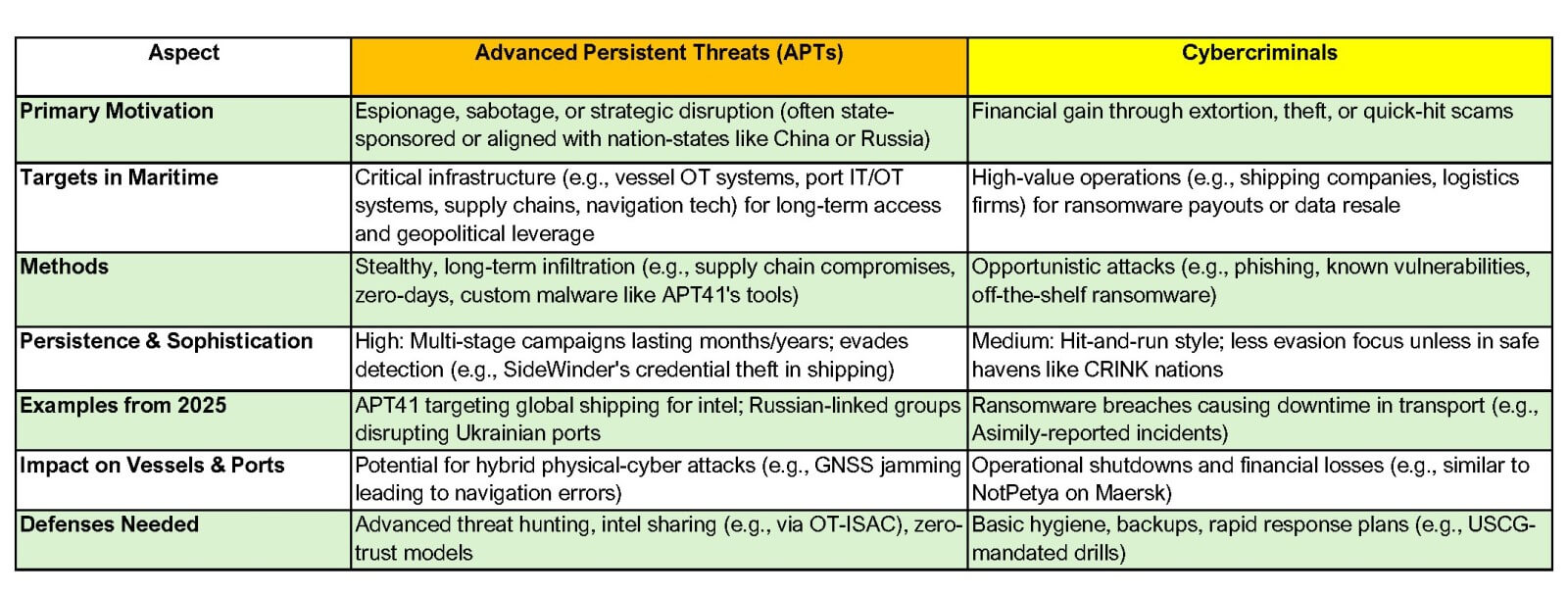
Cybercriminals and APTs: The Opportunists and Sneaks
Then there are the cybercriminals and APTs, chasing cash or secrets. Ransomware's exploding in 2025—ABS Consulting reported big breaches in transport causing shutdowns and lost bucks. The International Chamber of Shipping's 2024/2025 barometer ranked cyber as a top peril. See Table One (above).
APTs like SideWinder or China's APT41 are ramping up against shipping, slipping in via malware or supply chains. Cyble's July 2025 dive counted at least a dozen APTs hitting the industry amid tensions. They're after creds, certs, data—often paving the way for ransomware. Hacktivists pile on, messing with ports for causes. In Houston's OT-heavy world, one breach in petrochemical controls? Boom—safety nightmare.
From my InfraGard work, I know these groups evolve fast; staying ahead means constant vigilance.
What's Happened in 2025 and How We're Fighting Back
This year's seen a jump in attacks—Industrial Cyber noted hacktivists and states ramping up, including GPS tricks. And just this month, French authorities nabbed a Latvian crew member for planting malware—a remote access tool—on the Italian ferry Fantastic (owned by Italian shipping company Grandi Navi Veloci) while it was docked in Sète. The tool could've let outsiders remotely control the ship, but thankfully, the company spotted it, neutralized the threat without any real damage, and tipped off the cops. The guy's charged with hacking on behalf of a foreign power, with suspicions pointing toward Russian interference, as French Interior Minister Laurent Nuñez called it a "very serious matter" involving foreign meddling. A Bulgarian crewmate was questioned but let go. This kind of insider threat hits close to home for me—I've drilled teams on spotting these in OT environments, and it shows how even passenger vessels aren't immune, blending cyberrisks with potential physical sabotage.
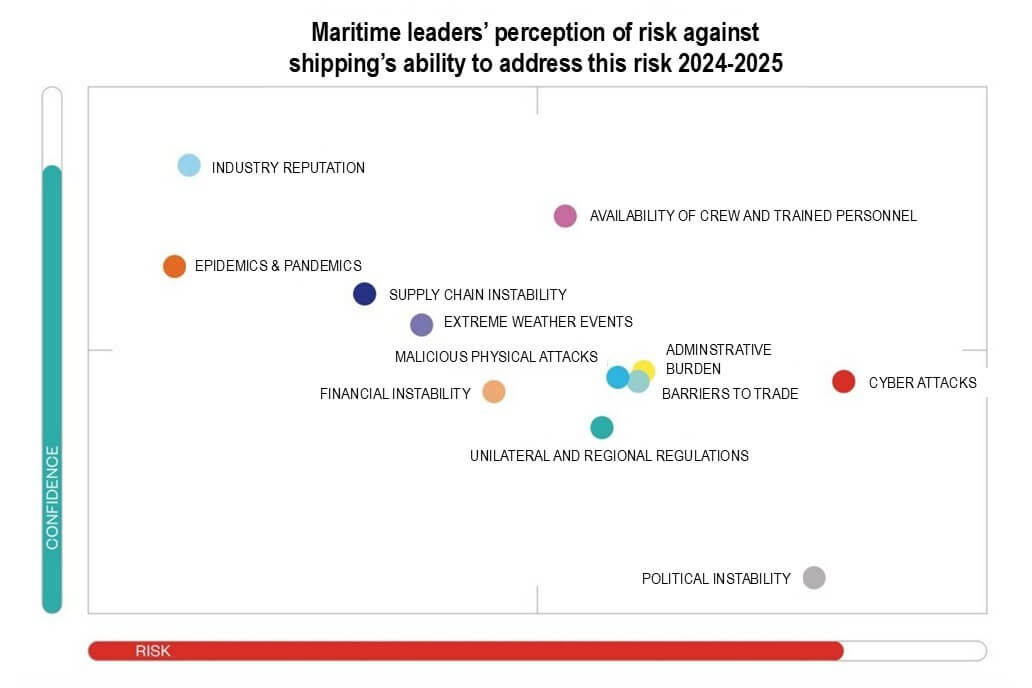
Globally, the Cyprus-Israel-Greece summit in December 2025 pledged a Maritime Cybersecurity Center. In India, IIT Kanpur's training and the new Bureau of Port Security focus on risks and sharing intel.
USCG's Cyber Protection Teams are hunting state actors, and insurers are demanding better coverage. ABS Consulting's 2025 take stressed endpoint security for offshore rigs. Closer to home, through InfraGard Houston and National, we've been pushing similar defenses.
Looking Ahead: 2026 Outlook
As we wrap up 2025, I'm already thinking about what's next—from my vantage point advising on port futures and training teams, the threats aren't letting up; if anything, they're getting sharper and more targeted. Windward's 2026 Maritime Forecast paints a picture of ongoing instability, with global trade routes caught in geopolitical tugs-of-war, like persistent Red Sea disruptions and Russia's expanding "dark fleet" using spoofed AIS and shady transfers to dodge sanctions. What worries me is the blend of cyber and physical—think undersea cable sabotage or AI-fueled data leaks from blurred enterprise-consumer tools, making maritime ops even riskier.
In transportation, the NMFTA's 2026 Trends Report warns of a surge in cyber-enabled cargo theft, where AI amps up social engineering for fake bills of lading or deepfake calls, compressing breaches to under an hour. Ransomware will evolve beyond encryption to pure extortion, hitting supply chains hard, while OT-IT gaps invite hybrid attacks on telematics and smart systems. Experts predict nation-states and criminals will ramp up on critical infrastructure like ports and logistics, using GPS jamming and one-day exploits for cyber-physical chaos. It's not all doom; with IMO's updated guidelines kicking in and regs like CIRCIA demanding quick reporting, we'll see more automated defenses and collaborations. But honestly, from my sessions, the key will be treating cyber as a full-spectrum issue—more targeted yes, but with the right prep, we can stay one step ahead.
Steering Toward Safer Waters
For the Greater Houston Port Bureau and folks like us, tackling this means a well-rounded strategy: pump money into AI monitoring, build those public-private ties, and stick to regs like the USCG's. Training's huge—I've seen it transform teams in my ISA sessions. But honestly, while threats keep morphing, our defenses can too. By leaning on innovation and staying alert, Houston can keep its edge in trade, even in rough waters.
About the Author

Marco Ayala
InfraGard National Sector Chief-Energy
International Society of Automation Fellow
infragard-houston.com

